Sundry Photography
Today I will be completing an in-depth analysis on Cloudflare (NYSE:NET). Within I will delve into the enormous opportunity the company has in front of it, provide a succinct overview of the company’s technology, and peek under the hood to see how the company is performing. In addition, I will discuss a series of positive and risk-based factors that I pondered while completing this analysis, perform an idealistic modelling assessment to gauge how expensive the company is, and more.
Introduction
Over the last few weeks, I have been picking away at the book “The Master and His Emissary”. Within, Ian McGilchrist analyzes the differences between the two hemispheres of the brain (the right and the left), explaining how their inherent functionalities may drive the contradictions we all feel in human existence. Without going into too much depth here (I encourage you to read his work instead), I found myself struck by the idea of The Belief in One Truth. In our modern society, which is so focused on intellectual excellence, any inconsistency in thought or theory is often considered an error or dysfunction. As a result, many are content to stick with the left hemisphere’s point of view, which can be easily articulated, in comparison to that of the right hemisphere, which is more ambiguous, harder to articulate, and often void of outright conclusiveness exhibited by its counterpart. The evolutionary change in our brain structures has resulted in human society as a whole becoming more left-hemispheric in nature, with individuals commonly holding beliefs that are rooted in supposed certainty, rather than accepting the fact that reality may be more complex. When I was performing my analysis for this report, I couldn’t help coming back to this concept. In particular, I was struck by the general acceptance of the working theory that the most Cloudflare was solely a CDN-centric company. Although direct parallels can’t be drawn between research on a tech company and a complicated analysis of neuroscience and philosophy, I found myself pondering the fact that this theory was left-hemispheric in nature, i.e. easy to articulate, in comparison to what I believe is a more nuanced story, one that I will be attempting to tell across this deep-dive. Before delving into that, it is worth discussing briefly how we got here.
As Cloudflare likes to point out, the internet in its earliest form was not built for what it has become today. Starting out as a medium for a few scientists to transfer files between their university computers, a feat that required a design of extraordinary complexity at the time, the internet now exists as a medium that billions of people interact with, powering the inner mechanisms of almost every business and economy known to man.
ARPANET Logical Map (Author)
As this technology scaled, and slowly intertwined itself with the fabric of modernity, problems started to arise. Traditionally, in the early days of the internet, webpages were loaded upon request on the end-user devices, as a result of direct interactions with the associated server. As you may have inferred, this can quickly become problematic when a large number of requests put strains on server resources, often resulting in poor performance or all-out crashes. CDN technology presented itself as a feasible solution to these aforementioned issues. Rather than having a user and a server interact directly with one another, the CDN acts as the intermediary, caching the response the server would normally give upon user request, distributing it across the CDN network, and then delivering it upon request. This is where distinguishing between static and dynamic assets becomes important. Static assets are the components of a website/app that don’t change when going from user to user, such as the navigation bar items for Netflix or the series of tabs on the left-hand side of the Twitter web app. Dynamic assets on the other hand require a heightened amount of computing resources in order to render, such as the unique home-feed content that will be displayed to a user, or the images that make up one’s social media profile often computed using centralized servers. CDNs are so powerful because static assets can be cached within these systems, allowing for certain components of a website/app to be processed closer to the end-user, filling in the dynamic assets thereafter, resulting in heightened and more responsive experiences as a result.
There is no doubt that the CDN and other associated application services became arguably the foundational tenets on which the company is built on. However, analysts solely focused on this offering are missing the point. Through the company’s vast array of offerings, they have successfully created an edge network highly in demand, are arguably at the forefront of the developments contained within Zero Trust security, and are taking on cloud providers head-on with their new cloud services offering. Cloudflare is much more than meets the eye and I will be attempting to quantify that for the remainder of this report.
With these ramblings in mind, let’s start to quantify the vast array of opportunities that Cloudflare has in front of it.
Opportunity
TAMs are typically large in stature, particularly when bolstered by high-flying tech companies. Be that as it may, there is no doubt that Cloudflare’s rapid development cadence and sturdy technological underpinnings have resulted in the company’s ability to target a wide array of end markets. A recent slide from the company’s Q2’22 investor presentation corroborates this assertion, showcasing the growth in opportunities the company has in front of it going from 2018A to 2024E:
Cloudflare’s massive TAM (Author)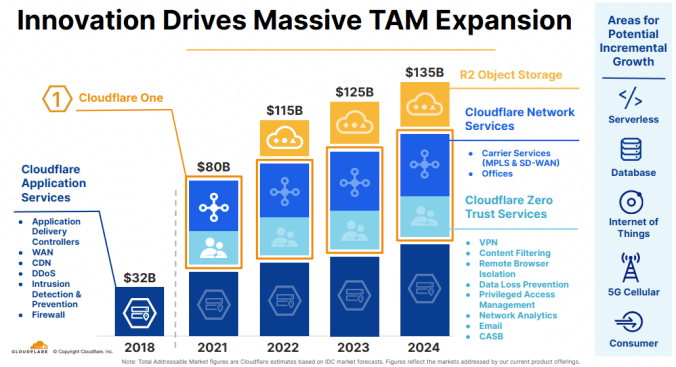
As outlined above, Cloudflare’s main opportunities can be split into four main components: Application Services and Network Services, Zero Trust Services, and R2 Object Storage. For the sake of brevity, I will stay surface-level on a few of these and go deeper into the opportunities that I, as an analyst, am most excited about. Starting off with Application Services, this offering is the company’s bread and butter, reliant and functional as a result of the expansive global network that Cloudflare has been building. As of right now, the company can reach nearly 95% of the world’s population within approximately 50ms of latency, has data centers situated across 275 cities and 100 countries, has 11,000 networks connected to it (including every major ISP and cloud provider), and has 155 Tbsp of global edge network capacity. As a result, the company can facilitate a plethora of development efforts through ADCs, WAN, CDNs DDoS, etc. Network Services leverages the aforementioned groundwork to offer customers additional functionality, allowing private area networks to be created, as an example. All of these capabilities are contingent on the fact that Cloudflare has built the infrastructure for, and exists as, an edge network. Therefore, the associated rise in edge computing is likely to result in a proportional increase in opportunities. As an example, the IDC anticipates that nearly half of new IT infrastructure will be at or reliant on edge networks, and by 2025 Garner predicts that approximately 75% of enterprise data will be created and processed outside the likes of a traditional data center or cloud provider, shockingly large prospects when one starts to think about it.
Moving on, the growth of Zero Trust as a whole will propel Cloudflare’s Zero Trust initiatives forward. Traditional methods of security rely upon what is known as a “Castle and Moat” system. In essence, these systems ensure heavily defend network perimeters, setting up plethoras of firewalls, intrusion detection systems, and a host of other security products in order to prevent external threats from compromising networks. This idealistic picture may sound somewhat secure, however, when company resources are scattered across cloud environments outside of their on-prem networks, it becomes harder to build a strong perimeter, and these systems often fail altogether when inside threats are present within the system. Similar to how the Trojan horse was used to breach the walls of the city of Troy, once an attacker gains access to the network, data and systems can be accessed therein, an unideal proposition to put it simply. Zero Trust changes all of that. Instead of assuming that entities within a network are all trustworthy, Zero Trust Security assumes that threats are present both inside and outside the network, distrusting everything by default. Zero Trust systems leverage micro-segmentation, multi-factor authentication, device monitoring, etc. in order to ensure entities are trustworthy before granting them access to any data or confidential/sensitive information. As you may have guessed, the pandemic-induced acceleration of expansive work-from-home trends only increased the rate of adoption across the world, forcing companies to examine the fragility of their networks as employees accessed their systems remotely at unprecedented magnitude. Uptake has been rapid and is estimated to continue growing in stature, with Garter anticipating that 60% of all organizations will embrace Zero Trust as a starting point for security by 2025 and Okta showcasing the fact that 97% of surveyed companies across the globe said that they have a Zero Trust initiative in place for the coming 12-18 months, a value that as only 16% 4 years ago.
ZT Survey (Okta)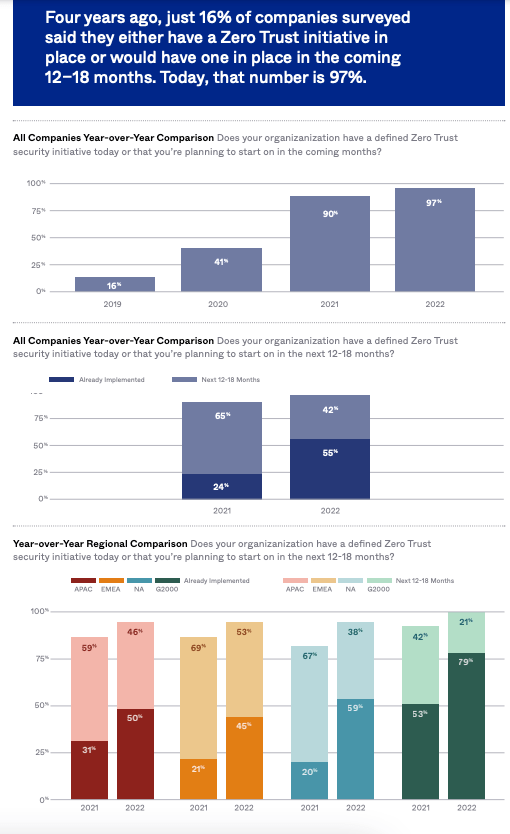
It can therefore be concluded with reasonable certainty that these trends will promote the uptake of Cloudflare’s Zero Trust services.
Lastly, it is worth touching upon the potential of R2, a product that is offering data storage capabilities that are very unique. As we all know, Cloud computing changed the world. Rather than having to build out capex-intensive projects that are a pain to maintain and operate, the cloud presented itself as a solution, allowing customers to access compute capabilities with rapid scalability, inherent flexibility, and top-notch security, at costs that would be almost possible to replicate on their own. With the rise in Cloud as a whole, Cloud storage also started to blossom. This tech allowed for IT departments to transform the cost of ownership, since with cloud storage there was no hardware to purchase, decrease time to deployment since the exact amount of storage can be made available to a customer upon request, and maintain strict information management standards.
On-Prem vs. Cloud (AWS)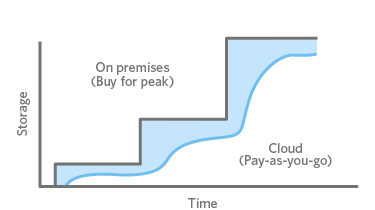
All of this sounds great, and by all means, it is, spare one eenie-meanie feature. As Ben Thompson points out within this enormous informative article, a downside exists when developers actually try to get their data back from these cloud providers. Most companies, over time, amass an abundance of data on their cloud provider networks, and, if they go to retrieve said data, they must pay huge egress fees. As an example, the returning egress traffic fee charged by AWS charges approximately $0.08-$0.12/GB, which is justified by this enormously complicated reference point. When viewed from the perspective of a traditional company, and given how much data these entities usually store, this toll is massive. Cloudflare’s ambitions in this area are simple, if they can offer low-cost storage services that treat don’t have these malicious pricing tactics, then they may have more and more developers build around this offering, resulting in heightened degrees of uptake, and a potential fourth cloud competitor as Cloudflare so ambitiously states. Only time will tell if these assertions come to fruition.
Technology
Cloudflare’s Integrated Global Cloud Platform can be split into three main components, their Global Network, the Edge Developer Platform, and a plethora of offerings that can be encompassed within Cloudflare One. I will spend time within this section breaking down each one.
Global Network
As alluded to earlier, the functionality of Cloudflare’s offerings as a whole is largely contingent on the stature of its global edge network. I have already outlined the expansiveness of the network that Cloudflare has created, however, it is pertinent to understand the building blocks off of which it was built, and which it functions. SSL/TLS functionality is leveraged to ensure secure communications occur between client and server, through email, and for other communications over unsecured networks. In essence, this process relies upon public key cryptography and asymmetric encryption in order to maintain connection security and ensure data safety. For Zero Trust security frameworks, a slight modification, i.e. mTLS (i.e. a two-way encryption verification instead of one) is often leveraged. The DNS capabilities, i.e. the ability for URLs to be routed to network IPs, of Cloudflare’s network are made possible through, authoritative DNS, where servers hold a copy of a regional phone book of sorts and match IPs with domain names, or recursive DNS, connecting to DNS servers that have the “phonebook” to a DNS server that has the required information. DNS capabilities go further through DNSSEC, a feature of the DNS system that authenticates responses to domain name lookups, particularly useful for preventing attacks from manipulating responses to DNS requests, or DNS over HTTPS which is a relatively infantile protocol that encrypts domain name system traffic passing through DNS queries. Lastly, Wireguard, leveraged in order to incorporate encrypted VPNs and decrease attack surfaces across the network.Outside of all of the building blocks mentioned above, the Global Network maintains adherence to a series of compliance and privacy best practices. These include a series of ISO standards, SOC (a voluntary compliance standard that specifies how organizations should manage customer data), PCI (payment card industry data compliance), and GPDR (general data protection regulation for logs and analytics). Lastly, Cloudflare offers customers access to their Data Localization Suite, where customers can control where their data is inspected, encrypt their data, control access to SSL private keys, choose where web traffic is handled and where log data gets sent, etc.
Edge Developer Platform
Cloudflare’s Edge Developer platform can be split into five distinct components: Workers, Workers KV, Pages, Durable Objects, and Video Streaming.
Workers
As I alluded to earlier, the workings of CDNs arguably transformed the internet as we know it, allowing for static webpage and application assets to be stored closer to the end-user, improving the experience as a result. Workers takes it a step further, allowing for dynamic assets to be stored in their data centers located across the world. In essence, workers allow for serverless functions to run as close as possible to the end user, a prospect that entails that the serverless code is “cached” on the network and runs when it receives an associated request.
Workers KV
While Workers essentially allows for dynamism to be stored at the edge, i.e. through the cache of serverless logic, KV is essentially a globally distributed key-value data store for the edge. This type of non-relational database is suitable for applications or processes with high data read requirements and low write requirements, allowing engineers and developers to create APIs and websites that respond in a similar expedited fashion to how static files would.
Pages
Cloudflare Pages is a JAMstack platform that allows front-end developers to collaborate and deploy websites. JAMstack is an architecture that has been seeing widespread adoption of late. On a technical basis, it allows for the entire front end of a website or application to be prebuilt into optimized static pages and assets. These assets can then be served using Cloudflare’s CDN. When viewed in conjunction with Workers and Workers KV, it is clear that Cloudflare is allowing full-stack applications to be created on the edge, where static assets can be created and stored using pages, and dynamic functionality and associated data requirements able to be stored on the edge using Workers and Workers KV.
Durable Objects
Durable Objects offer two primary forms of functionality, storage, and coordination. The former, boiled down to the simplest unit of simplicity, essentially allows for developers to leverage the fact that storage is co-located with an object, whereas the latter allows for requests to be made to the same topic/process. Since requests from the same topic are forwarded to the same object, coordination can be made between them. In practice, these can be thought of as database-esque entities that serve a specific purpose, holding data that a group of workers may need, remembering any changes that have been made to said data over time, in comparison to traditionally stateless computing that usually occurs on the edge.
Video Streaming
This offering was brought to market in order to combat the issues that plagued streaming businesses for so long. Now, developers can leverage the Cloudflare edge network to compress cache videos, record, play, and even live-stream videos, if desired.
Cloudflare Application Services
As I alluded to earlier, application services are Cloudflare’s bread and butter, offerings that blossomed from the company’s strong edge network, which will continue to be a strong foundation going forward.
CDN and DNS
With their CDN, Cloudflare allows for developers to cache static content, accelerate dynamic content through the aforementioned edge developer platform capabilities, and optimize outbound content. In addition, their CDN optimizes content based on device, browser, and bandwidth requirements. Cloudflare also operates a public DNS resolver, denoted 1.1.1.1, which offers a fast and private way to browse the internet. DNS is essentially phonebooks of the internet, essentially translating domain names into IP addresses so that users can access a website without having to know the site’s IP address itself (i.e. your computer actually doesn’t know where google.com is, it requires an IP address and DNS systems allow for this to be possible).
L7 DDoS Protection
A DDoS attack is an attempt to disrupt the functionality of a server or network infrastructure by directing high amounts of traffic at a component of said infrastructure in order to overwhelm the system. Layer 7 DDoS attacks are often facilitated through the use of HTTP GET, commonly bypassing the TCP layer, and appearing legitimate enough to be passed on to the web or application server. The attacker then requests large amounts of files/objects through HTTP GET, overwhelming the server with the sheer volume of requests, and disturbing infrastructure as a result. Cloudflare’s edge network is DDoS protected, which essentially means that traffic is monitored, ensuring that only verified user traffic is able to go through, operating on four key mitigation principles:
DDoS Mitigation Stages: Cloudflare.com (Cloudflare)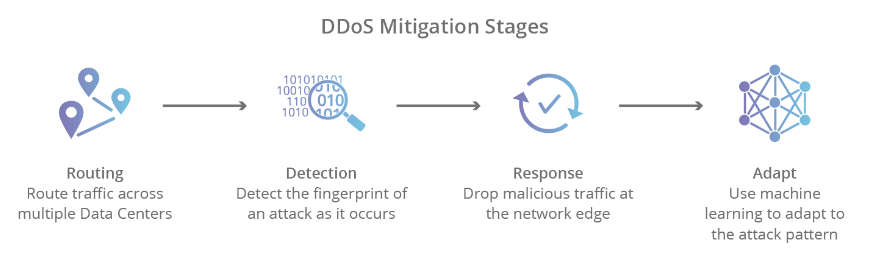
Bot Management
Bot traffic (i.e. any non-human web traffic) is problematic for websites and applications because it can put increased loads on servers, and poses security threats as some bots are able to spread spam, steal user credentials, etc. Cloudflare’s bot solution monitors automated traffic to protect resources from bad bots, a phenomenon achieved through behavioural analysis, machine learning processes, and fingerprinting applied to customer traffic.
Load Balancing
Having server systems that are either stressed through over-utilization or distant from end-users, degrades application performance and hurts user experiences. Cloudflare Load Balancing essentially redistributes traffic away from the unhealthy or unresponsive components of the server network, reallocating it to pools of servers with higher performance.
Rate Limiting
Rate limiting is a usage cap that is applied to network traffic, preventative measures that are taken against bot activity that can prevent the over-interaction with certain components of an application or webpage, which strain server functionality and performance. Cloudflare’s rate limiting functionality monitors application activity, tracking IP addresses making requests, and the amount of time that exists between each request, ensuring that any potential bad actors are blocked from making any additional requests for a certain amount of time if they have been flagged, freeing up resources as a result.
WAF with API Protection
Cloudflare offers customers access to a WAF (web application firewall) that prevents common attacks such as cross-site forgery and scripting, SQL injection, etc. This is achieved through the filtering and monitoring of traffic that occurs between the web application and the internet, existing as a reverse proxy that ensures traffic passes through and is verified for safety before being passed through to the web server.
Network Services
WAN-as-a-Service
A WAN, put simply, is a large network that connects a group of computers over large distances and is commonly used by large businesses to connect their office networks. The two common methods used to create these WANs are MPLS services, or IPSec VPNs. The MPLS methods are reliable but expensive and IPSec VPNs are cheaper but often less reliable. Both the former and the latter struggle with the modern tech stack, excelling with traditional infrastructure reliant on data centers and in-office work, faltering with heightened instances of applications existing in the cloud and remote work. WAN-as-a-service allows for companies to bring geographically dispersed data centers situated across offices, devices, and cloud environments into a single cloud-managed WAN, supporting a host of different on-ramp mechanisms for businesses to connect their traffic to Cloudflare’s network.
Firewall-as-a-service
FaaS exist as a product that filters out malicious network traffic, blocking and allowing traffic based upon a certain set of rules, enabling network rules to be enforced at the edge. As a result, a virtual barrier of sorts is able to exist around a company’s network, capable of protecting on-prem and virtual infrastructure, offering top-notch functionality that doesn’t have to be maintained through an appliance.
L3 & L4 DDoS Protection
Unlike the layer 7 DDoS attacks mentioned earlier, which mimic real human behavior, and overwhelm the server with legitimate-looking requests, layer 3 or 4 attacks see network layers and transport layers tested. Cloudflare’s technology protects against these attacks for all TCP/UDP applications and on-prem, cloud and hybrid networks.
Network Interconnect
Cloudflare Network Interconnect allows customers to set up physical or virtual interconnections, using technology such as interconnect partners or internet exchanges, in order to derelict traffic away from the public internet onto Cloudflare’s edge network, boosting performance as a result.
Smart Routing
Public internet, though functional, occasionally struggles when network congestion occurs. Cloudflare leverages data from its 10 trillion global requests per month in order to detect when real-time congestion occurs, and re-route traffic across the most efficient path of their edge network accordingly.
Zero Trust Services
Zero Trust Services are encompassed within the Cloudflare for Teams product suite, an offering that was announced in 2020 in order to provide functionality that addresses the majority of every IT organization’s challenges.
ZTNA with Private Routing
Zero Trust Network Access is the very foundation of how a Zero Trust security model can be implemented and enforced. Functioning similar to software-defined perimeters, the ZTNA ensures that devices are not aware of any applications or services on the network outside of what they are connected to, reverifying and recreating permissions and credentials periodically. As a result, secure boundaries around applications are created. In essence, users can connect to corporate resources through clients or web browsers, which are then routed through Cloudflare’s edge network, and evaluated against predefined Zero Trust rules in order to ensure safety and legitimacy.
Author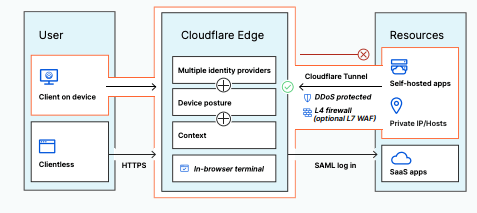
Remote Browser Isolation
Cloudflare browser isolation in essence executes content remotely, away from the endpoint, separating the process of loading webpages from the actual user device rendering said webpage. As a result, this ensures that any webpage code doesn’t run on the user’s device itself, preventing malware infections and other forms of cyber attacks from being successful.
SWG with CASB
SWGs (secure web gateways) are proxy servers that make requests and receive responses on behalf of a client device. The gateway inspects the request and only passes it along if it doesn’t violate security policies. When combined with CASB (Cloud access security brokers), i.e. entities that complete security capabilities ranging from identifying verification, access-control, sandboxing, urlfiltering, etc., Cloudflare is clearly focusing on offering solutions, that protect traffic to and from corporate SaaS applications, amongst other things.
Identity/Endpoint Integration
Lastly, Cloudflare has partnerships with companies ranging from the likes of CrowdStrike (CRWD) and SentinelOne (S), on the endpoint side of things, to identity managers like Okta, allowing for a full and all-encompassing Zero Trust functionality when viewed in conjunction with the features mentioned above.
Financials
Within this section, we will be taking a look at the company’s most recent annual and quarterly income statements, balance sheets, and cash flow statements. All dollar values mentioned herein are in millions of USD.
Income Statement
Revenue
Starting off with top line, Cloudflare’s revenue has grown at an insane 51% CAGR on an annual basis, coming in at $656.4M for FY’21, representing a 52% increase on a YoY basis. Quarterly results were also impressive, demonstrating strength in the face of uncertainty, with Q2’22 revenue coming in at approximately $234.5M, representing a 54% and 135% YoY and Yo2Y increase, respectively.
Change in Revenue – Annual (Author) Change in Revenue – Quarterly (Author)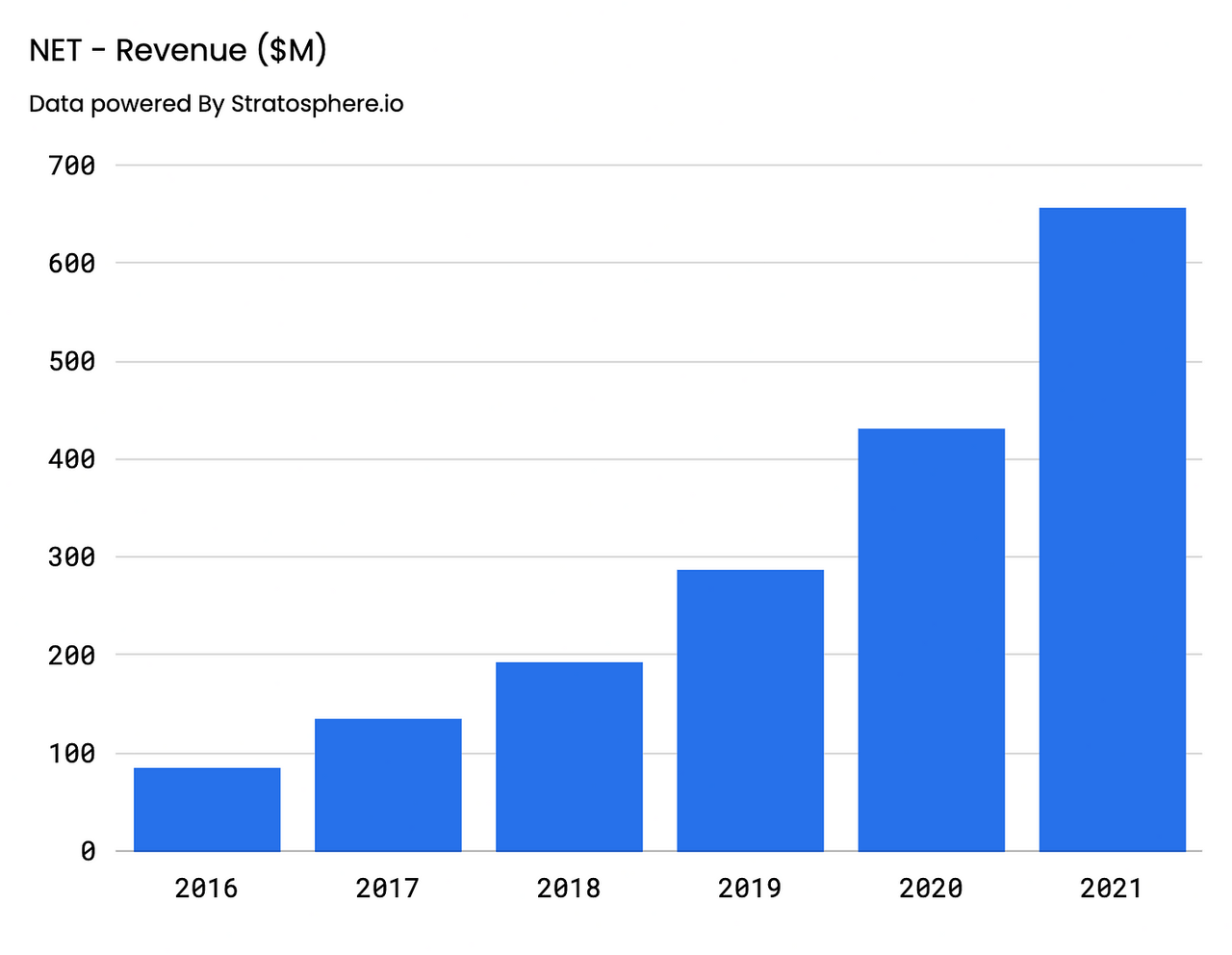
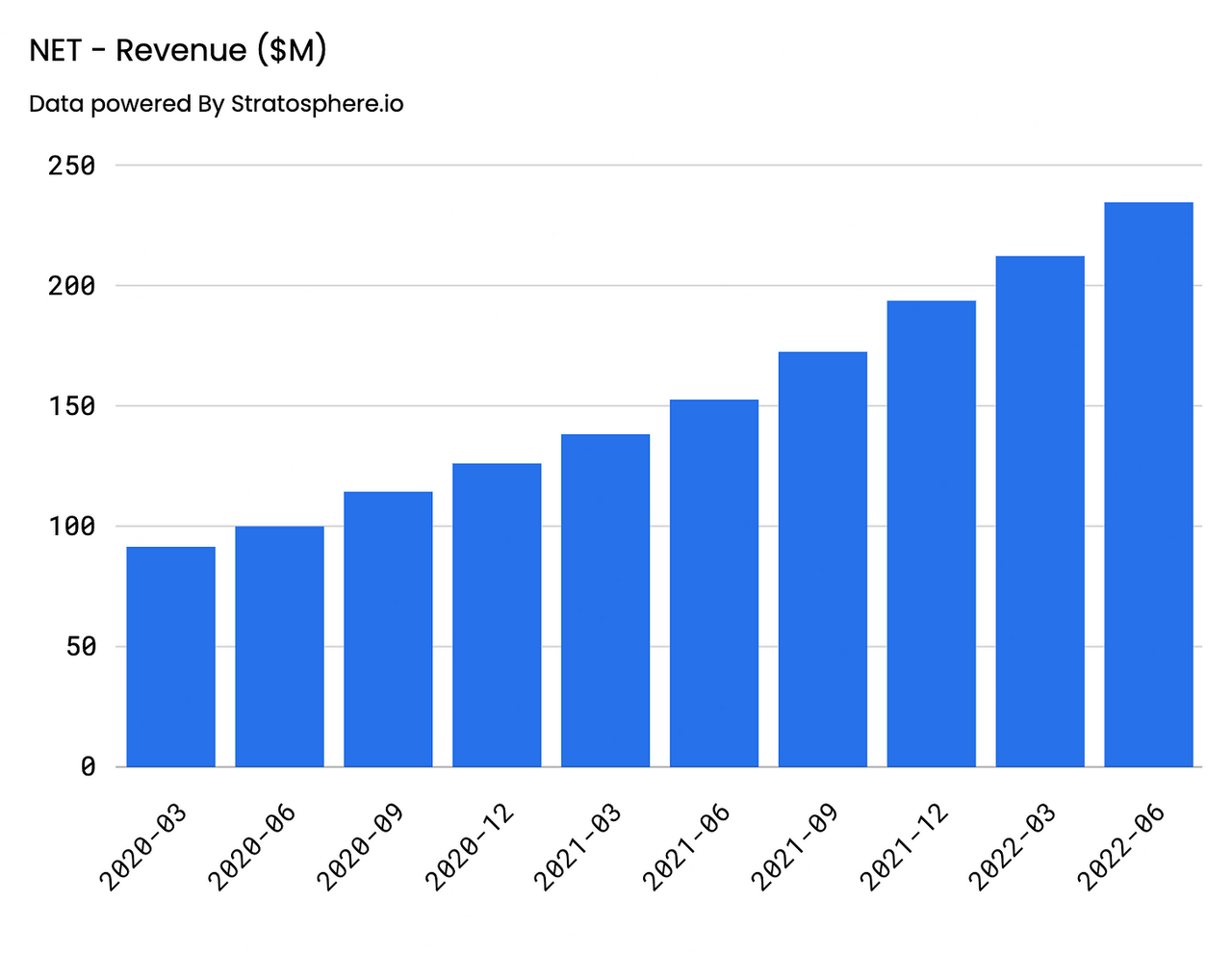
Strategically speaking, the most recent quarter’s strong performance, according to management, was largely reflective of the company’s upmarket tactics they have been employing of late. In other words, Cloudflare has clearly been targeting larger customers, a phenomenon that is reflected in the fact that 60%+ of Revenue in Q2’22 is attributable to large customers, in comparison to 50% at the same time last year. This is also observable with the decline seen in SMB customers relative to the top line, a value that represented approximately 11% of revenue in the second quarter in comparison to 14% last year.
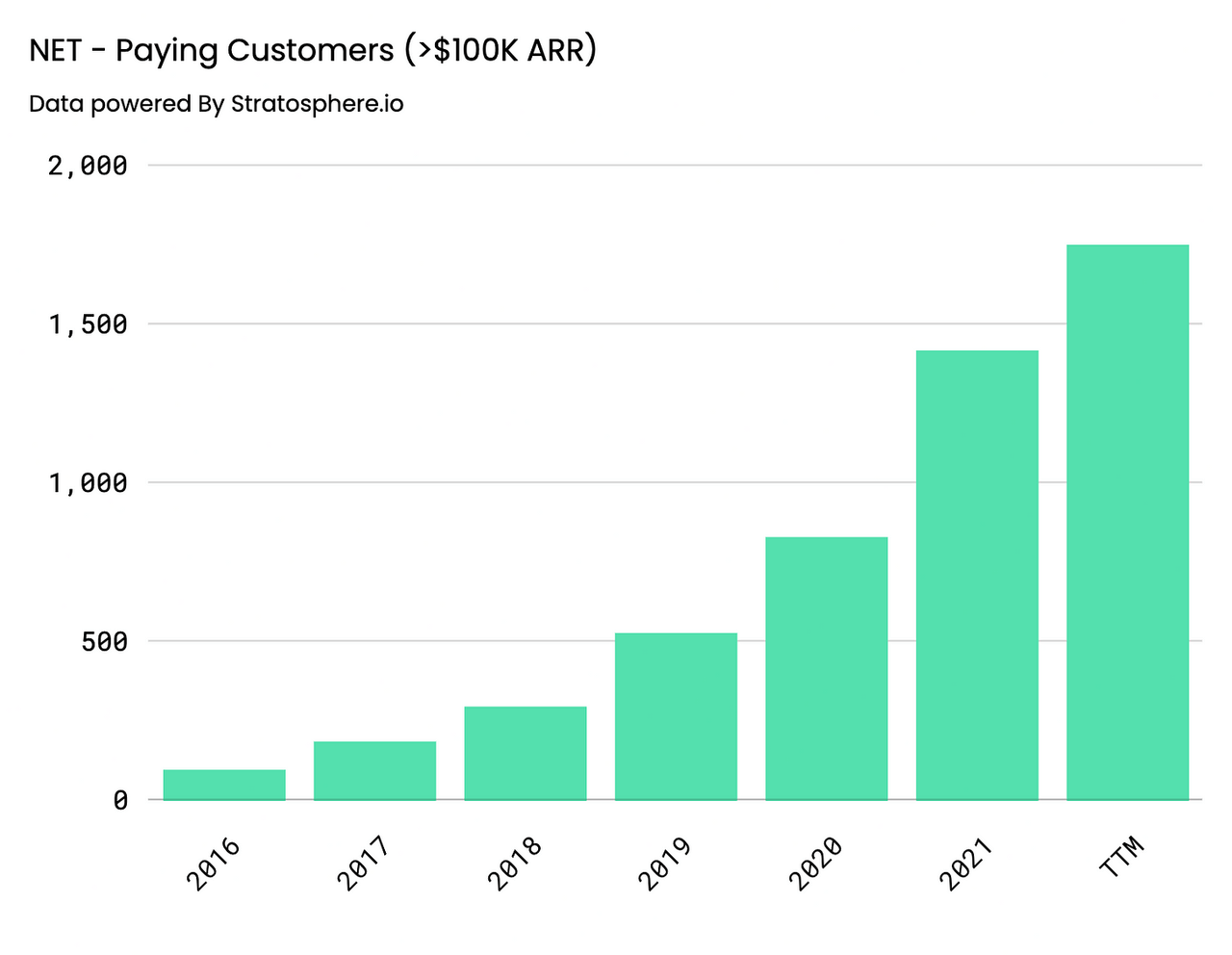
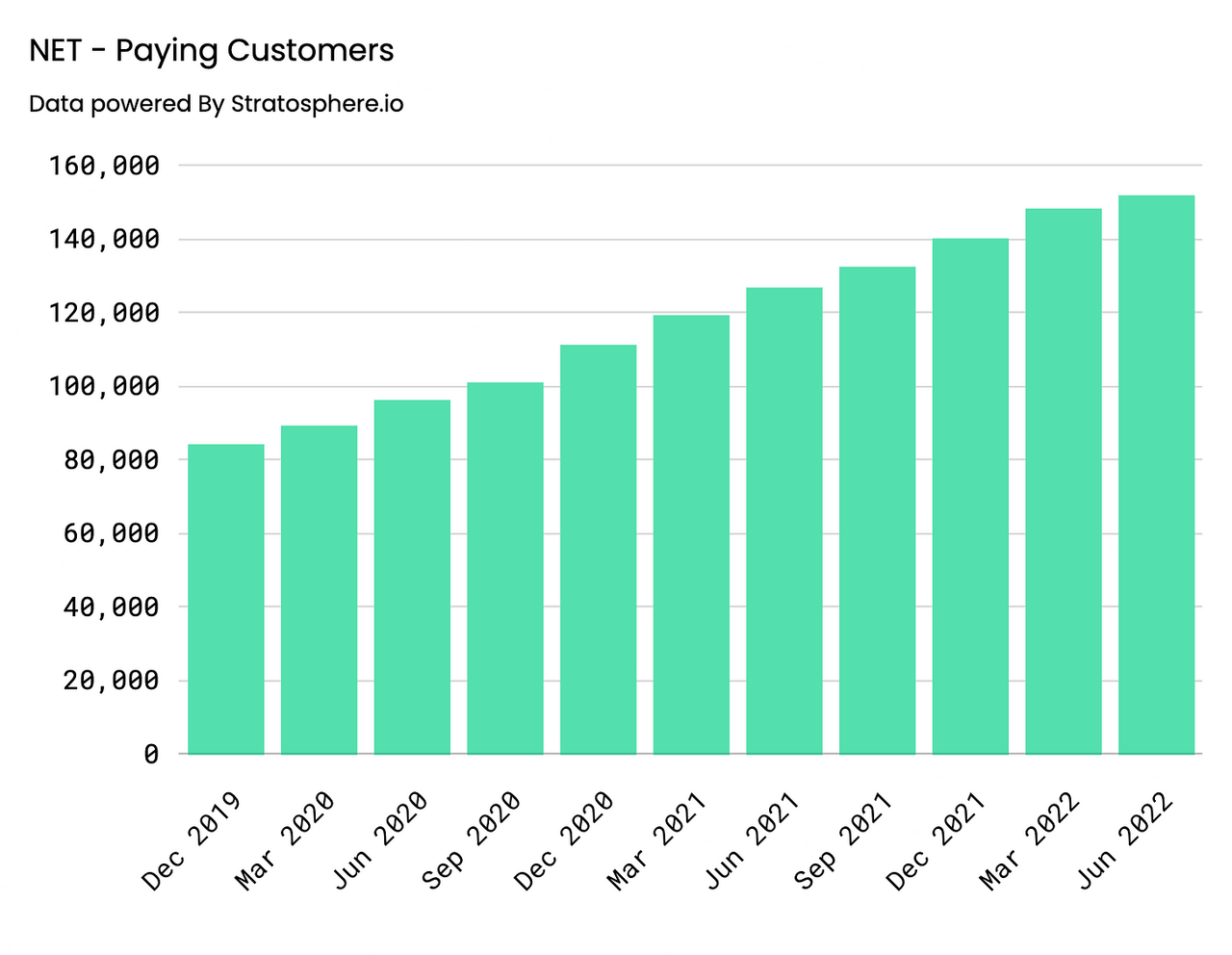
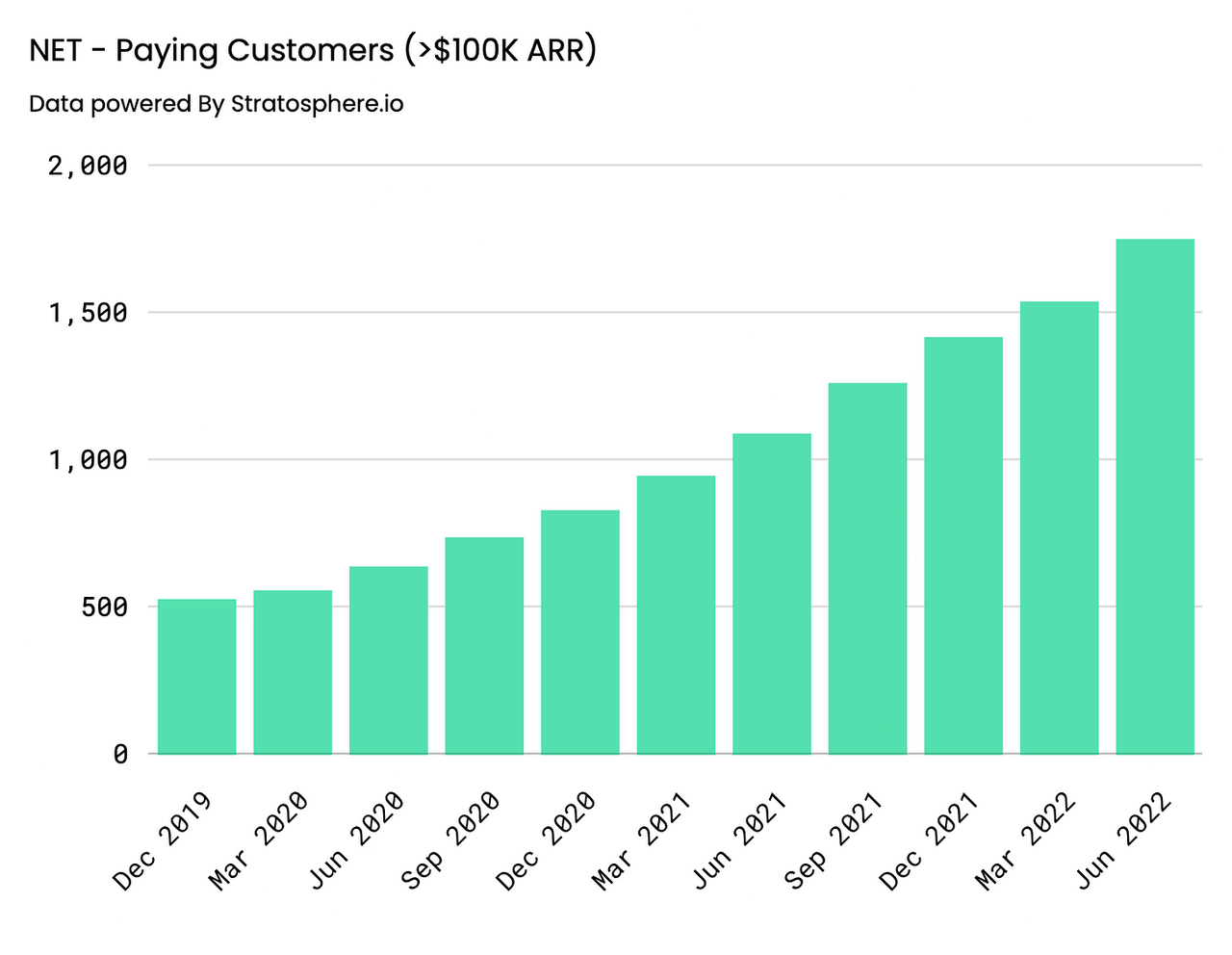
Key Performance Indicators continue to signal business strength as well. On an annual basis, customer growth has been steady with Paying Customers increasing 26% YoY, coming in at 140,096, and Paying Customers with >$100K in Revenue growing 71% YoY, coming in at 1416. Similar behavior can be observed on a quarterly basis, Paying Customers increased 20% and 58% YoY and Yo2Y, coming in at 151,803, whereas Paying Customers with greater than >$100K in Revenue came in at 1749, representing a 61% and 175% YoY and Yo2Y increase, respectively.
Paying Customers – Annual (Author) Paying Customers > $100K ARR – Annual (Author) Paying Customers – Quarterly (Author) Paying Customers > $100K ARR – Quarterly (Author)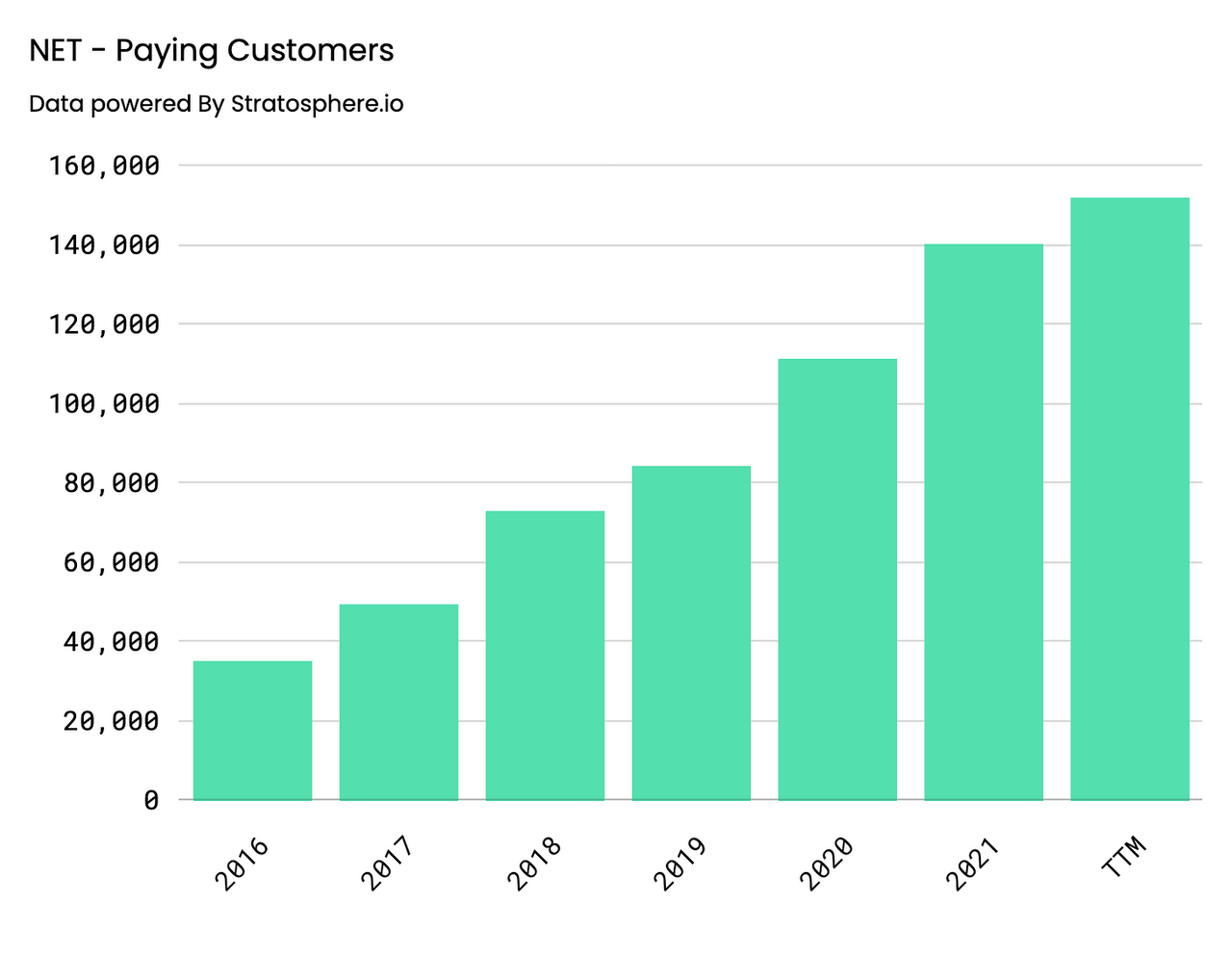
In addition, Dollar-Based Net Retention Rate (DBNRR) remains high, coming in at 125% for FY’21 in comparison to 119% in FY’19, and 126% in Q2’22 in comparison to 124% and 122% in Q2’21 and Q2’20, respectively. Management is adamant about getting this metric above 130%, and with their ever-expanding product suite, they likely will in the coming years, even despite the challenging macro environment. Lastly, Remaining Performance Obligations are approximately 76% of Current RPO and came in at approximately $760M for the quarter. On a geographic basis, top line has stayed relatively consistent, both annually and quarterly, when split into geographic segments. The company evidently derives the majority of its revenue from the US, followed in order of descending magnitude by Europe, the Middle East and Africa, APAC, and Other regions:
Author Author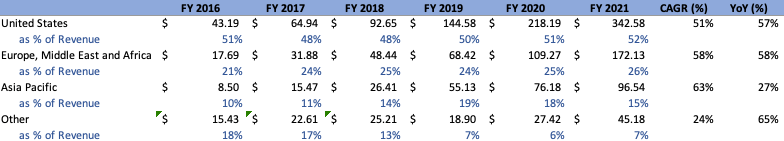
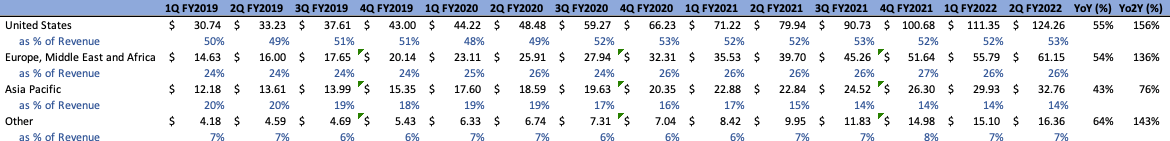
Looking forward, macroeconomic situations will evidently come into play when analyzing the strength of demand in different regions. Europe and Japan in particular have been particularly impacted by currency headwinds, being that Cloudflare’s products are denominated in USD. Coupled with the fact that these regions have economic outlooks that are potentially looking more bleak than that of the US, it is not unreasonable to think that, even despite Cloudflare’s mission-critical products, headwinds may be looming around the corner. Something to monitor going forward at the very least.
Lastly, as a company, from a sales strategy perspective, Cloudflare is still evidently heavily reliant on direct partners rather than channel partners:
Author Author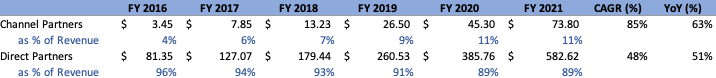
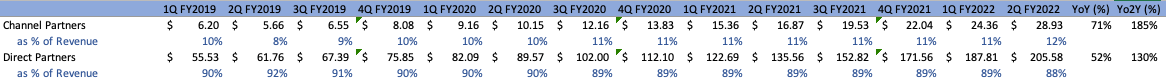
Although this phenomenon is likely to continue going forward the company is increasingly reliant on channel partners in order to distribute its Zero Trust products. As mentioned within the Q2 conference call, the company has obtained half of Zscaler’s channel partners and is leaning on their recent Area 1 acquisition, seeing as the company has sophisticated channel programs already in place.
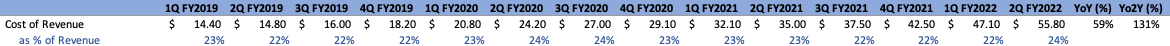
Cost of Revenue
For FY’21, COR increased at a slightly lower rate than the top line, coming in at $147.1M, a 45% YoY increase and 44% CAGR from FY’16. Relatively speaking, this value has stayed consistent, coming in at 22% of the top line, a value that has oscillated between 21% and 23% over the last few years. On a quarterly basis, COR increased slightly more than top-line YoY, coming in at approximately 24% of revenue, at $55.8M, a 59% YoY increase.
Author Author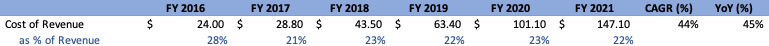
Gross Profit
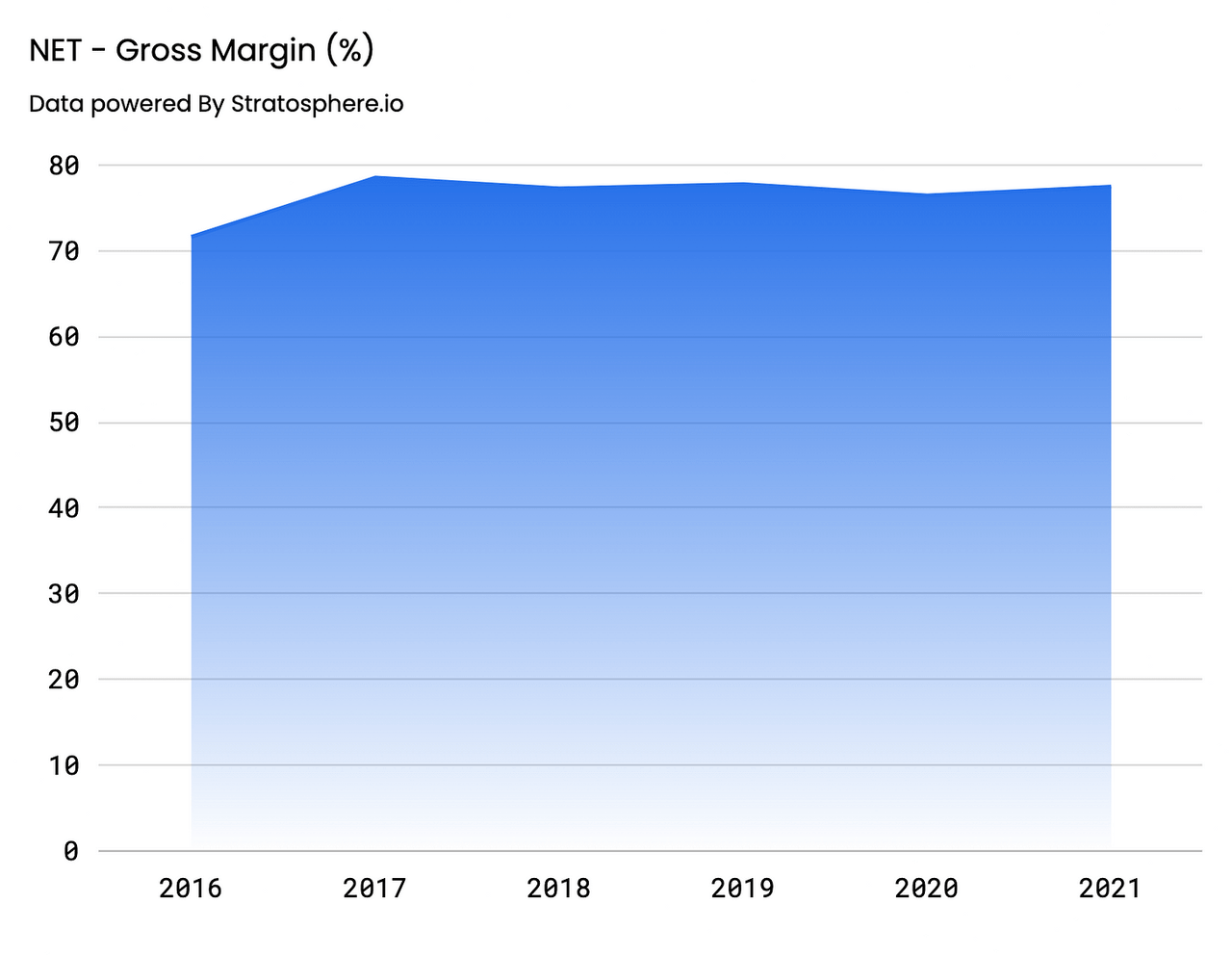
GAAP Gross Profit came in at approximately $509.3M for FY’21, representing a 54% increase YoY and a 53% CAGR from FY’16. Gross Margins have stayed consistent on an annual basis, glued in the high 70% range, with FY’21 GMs at 78%. On a quarterly basis, Gross Profit increased at a slightly slower rate than the top-line at 52%, coming in at $178.7M, representing a Gross Margin of 76%. Going forward, investors should anticipate that this value remains stable in the mid-high seventies.
Gross Profit – Annual (Author) Gross Margin – Annual (Author) Gross Profit – Annual (Author) Gross Margin – Quarterly (Author)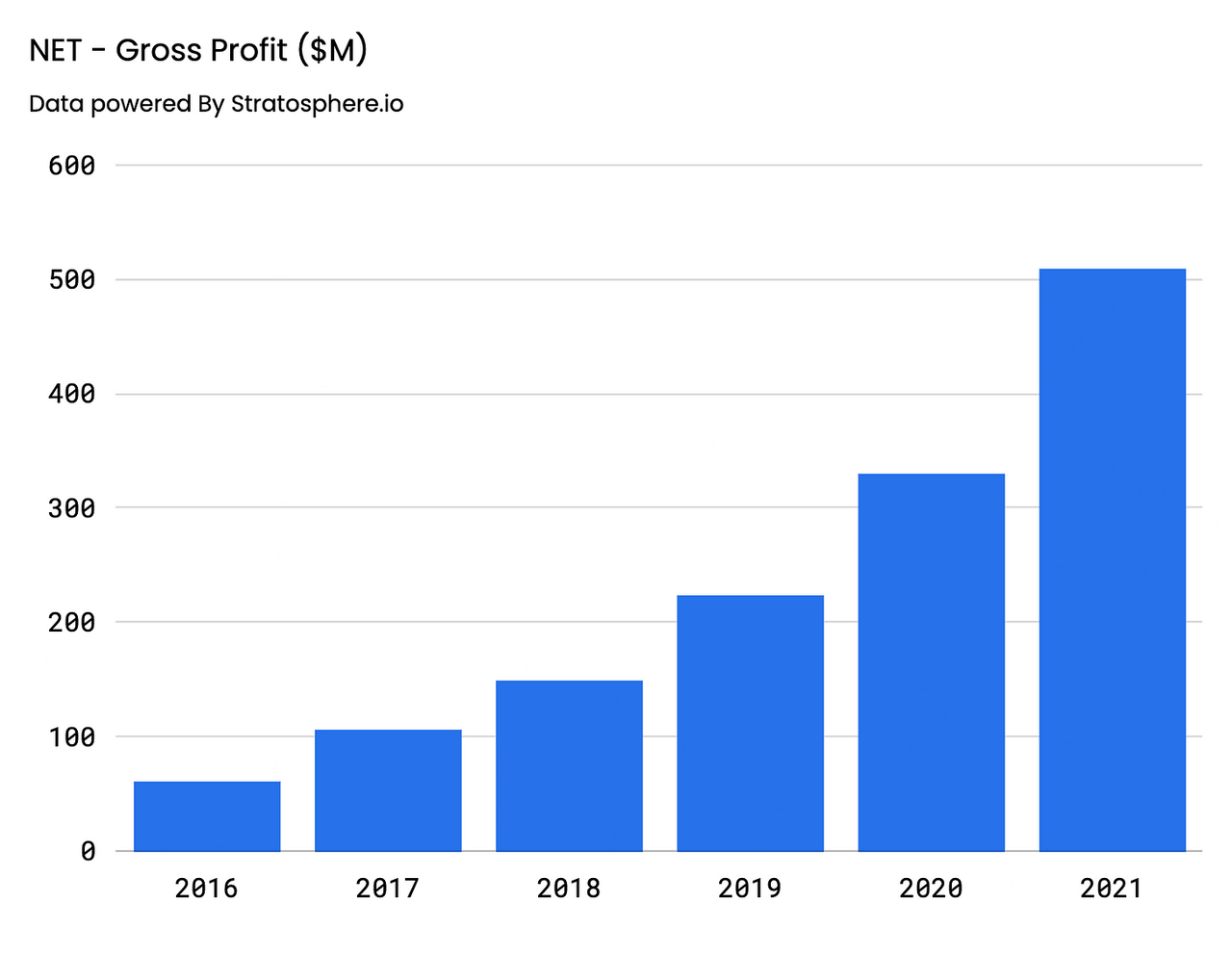
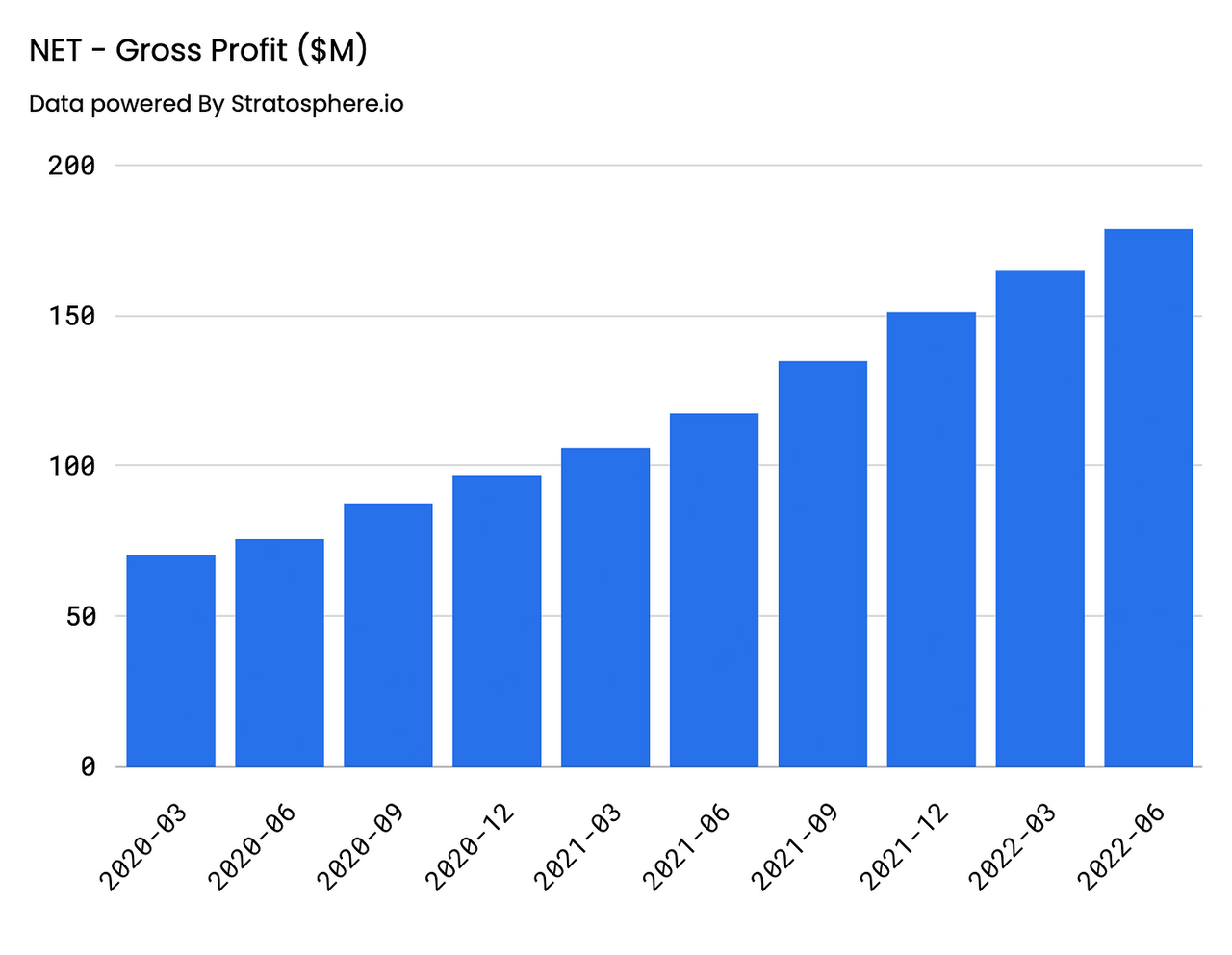
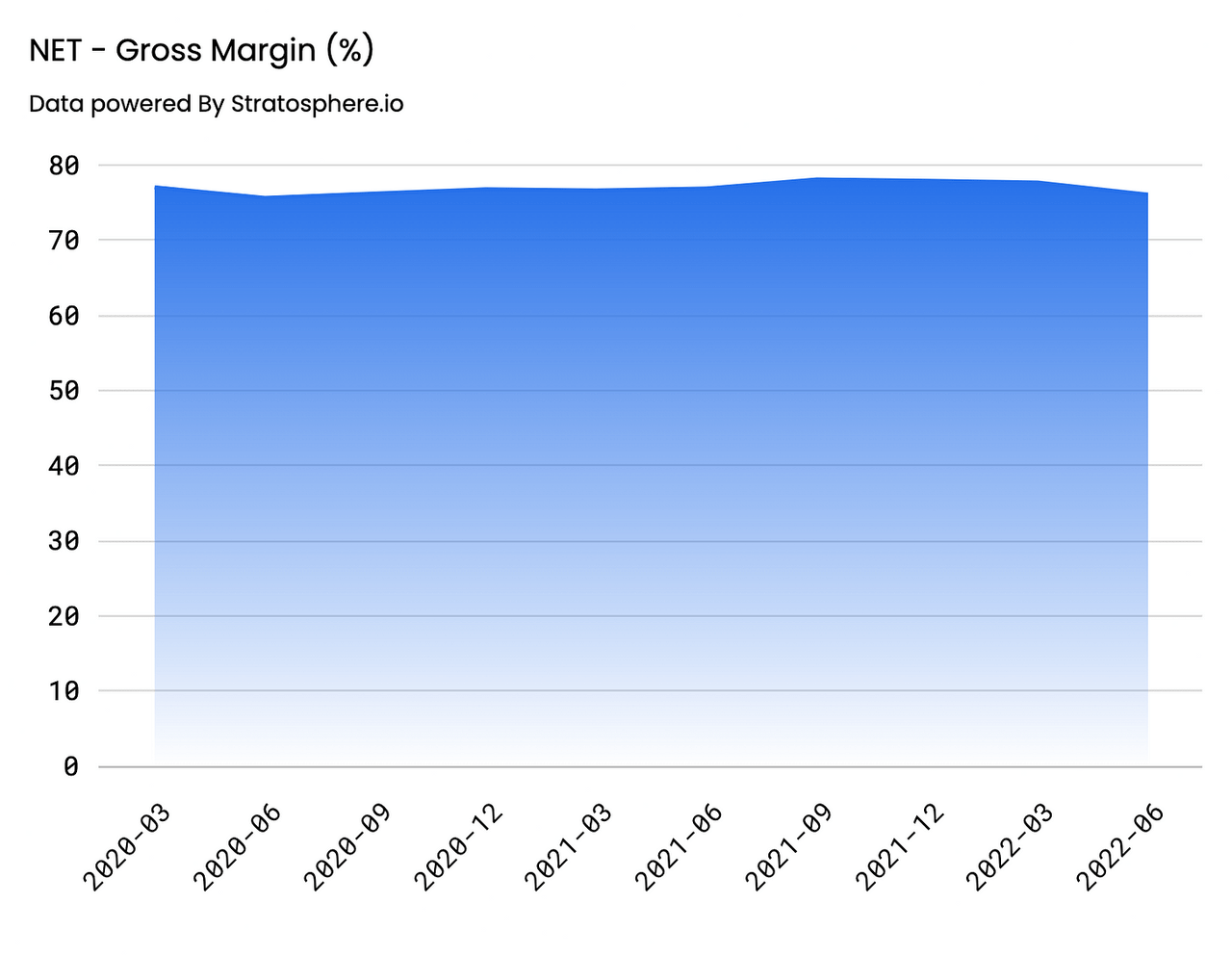
Operating Expenses and Margins
Management has been pretty adamant on the fact that they intend to keep operating their business in a slightly negative or breakeven manner (as gauged by operating margins) as long as they are able to sustain commendable growth. As such, this should continue to be the behavior investors expect going forward. Total OPEX for FY’21 came in at approximately $637M, representing a 46% increase YoY and 52% CAGR from FY’16, decreasing relative to the top line in comparison to the year prior. As a result, Operating Margins were approximately -19%, representing an Operating Loss of approximately $(128)M. Net Income and EBITDA values paint a similar picture, with EBITDA margins improving slightly YoY to -13% and Net Income coming in at -40%, values that would’ve shown improvement if they were not for the one-time $(72)M loss associated with the extinguishment of debt. The distribution of Total OPEX into its constituents, as well as the change in margins over the years, can be seen below:
Author Author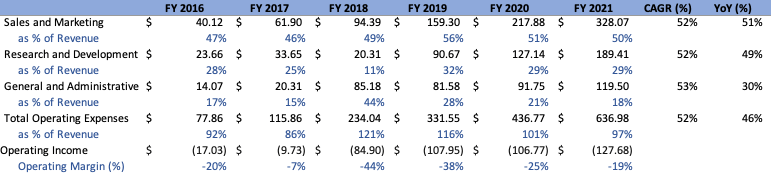
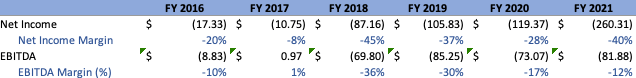
On a quarterly basis, Operating Margins deteriorated slightly in comparison to the previous Q2s, coming in at -28%, resulting in an Operating Loss of approximately $(65.5)M. This phenomenon was primarily driven by increased hiring efforts, with Cloudflare increasing total employees by 49% YoY, with 3060 being the company’s new headcount. Both Net Income and EBITDA margins exhibit similar behavior, slipping slightly more negative and coming in at -27% and -21% for Q2, respectively:
Author Author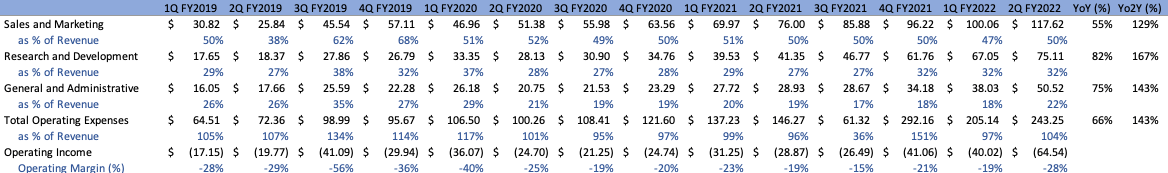
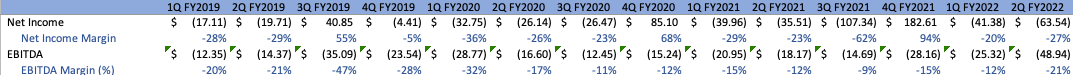
Outside of their go-to-strategies, Cloudflare intends to slow down expansionary efforts heading into the remainder of the year, a phenomenon that should result in margins stabilization and improvements, as Cloudflare reaps the benefits of their ever-expanding network and the fact that most of their expansionary investments, outside of hiring, are capex-intensive and are not being done using the income statement.
Balance Sheet
The change in Cloudflare’s balance sheet from the end of last year to the most recent reporting period, Q2’22, can be seen outlined below:
Author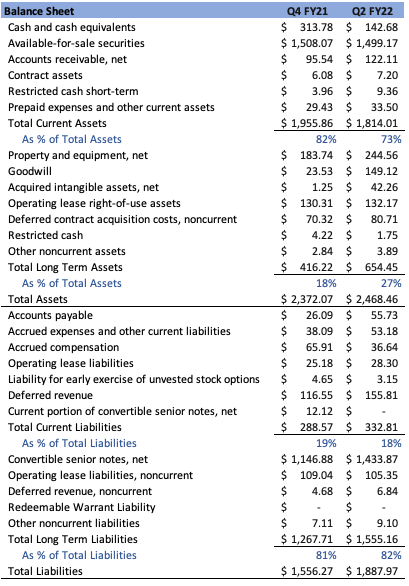
The company has a strong balance sheet, and its assets are predominantly liquid. Current Assets make up 73% of Total Assets and are composed predominantly of Available-for-sale securities, Cash and Equivalents, and Accounts Receivable. Long Term Assets increased relatively speaking, coming in at 27% of Total Assets and consisted mainly of PP&E, Goodwill, Operating Lease Assets, Deferred Contract Acquisition Costs, and Acquired Intangibles, in order of descending magnitude. Liabilities are primarily non-liquid, with Current Liabilities at 18% of Total Liabilities, primarily comprised of Deferred Revenue, Accounts Payable, Accrued Expense, Accrued compensation, and Operating Lease Liabilities in order of descending magnitude. Long Term Liabilities are 82% of the total, comprised primarily of Convertible Senior Notes and Non-Current Operating Lease Liabilities, in order of descending magnitude. Moving forward, I don’t anticipate the company’s balance sheet to be a source of a hindrance.
Cash Flow Statement
The change in Cloudflare’s various cash flows, both annually and quarterly, can be seen outlined below:
Author Author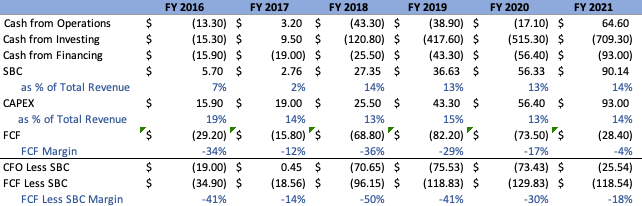
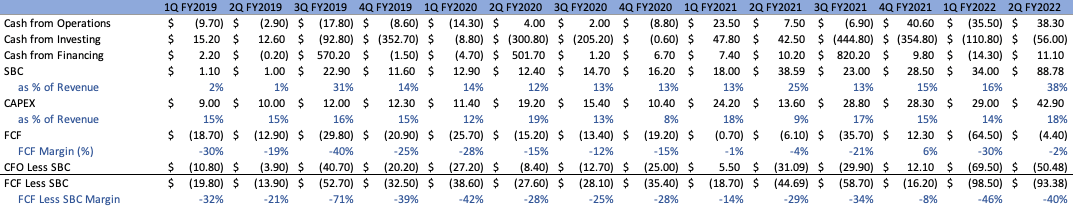
Honing in on Q2’22, CFO in at approximately $38.3M. CFI came in at approximately $(56)M, an outflow primarily resulting from the purchases of available-for-sale securities, acquisitions, capex, net cash acquired, and capitalization of internally used software, offset by the sale of mature securities. CFF came in at approximately $11.1M, attributable primarily from the proceeds of stock issuance and the exercise of stock options, offset by the repayment of senior notes and payments related to RSU settlements.
There are most definitely some interesting developments here. First off, after a Q1 that was relatively disappointing, Cloudflare got closer to their goal of maintaining only slightly negative FCF for the quarter, with FCF margins at -2%, values that are significantly more negative if we take into consideration SBC adjustments, with FCF less SBC margin at -40%. This is evidently a result of the company’s large investments being made in talent, a value that should stabilize given their plans to slow down on this behavior. Next, it is clear that the company has been maintaining a significant degree of investment into their network infrastructure, corroborated when we see CAPEX as a % of top-line steady in the high teens. Management stated that this should stabilize in the 12-14% range in the future. Although Cloudflare is more capex-heavy than a lot of modern tech companies, this strengthens its position in a two-fold manner. Firstly, a geographic presence that is worldly in nature is something that a lot of edge-network and CDN providers do not bolster, and Cloudflare is cementing, if not continuing to increase, their standing as a result. Customers and users alike despise latency and having a presence close to the end-user are immensely valuable. Second, this allows for Cloudflare to reap the rewards of fixed cost structures vs. incremental costs. As we are all aware, cloud infrastructure is the foundational pillar of almost every piece of modern technology, primarily operating on a usage-based volume, charging customers as their products gain popularity and see heightened traffic as a result. Cloudflare on the other hand doesn’t have this issue. Being that they are reliant on their own infrastructure to function, they have significant operating leverage levers to pull going forward.
Discussion
Now that we have an understanding of the company’s past and present, obtained through a look at their current tech offerings and previous financial performance, it’s time to look towards the future and discuss what may be looming over Cloudflare’s horizon. Starting off with guidance, the company beat all expectations for Q2, as outlined below, a phenomenon that should come as no surprise given the average sales surprise we’ve seen over the quarters since they went public:
Cloudflare Earnings Summary – Consensus Gurus (Consensus Gurus)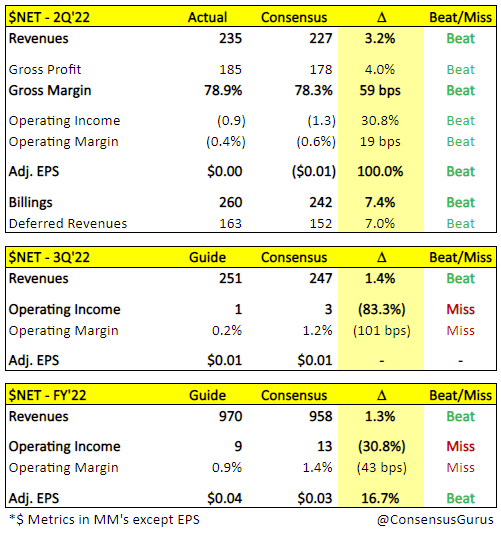
The company also raised top-line guidance for both the upcoming quarter, Q3, and for FY’22, with adjusted EPS remaining flat and being raised for the former and the latter, a respective feat given market dynamics. On the opposite end of the spectrum, Cloudflare lowered guidance for operating margin by approximately 100 and 40 bps for the aforementioned periods, actions that are not deleterious by any means given the fact that they align with the company’s plans to maintain commendable growth while operating their business in a breakeven manner.
Moving on, Cloudflare is quite evidently valued richly. Despite, selling off in unison with tech post-Jackson Hole, the company still bolsters the highest forward EV/Rev multiple amongst its high-flying peers:
Top 10 Valuations, Cloud Software (Author)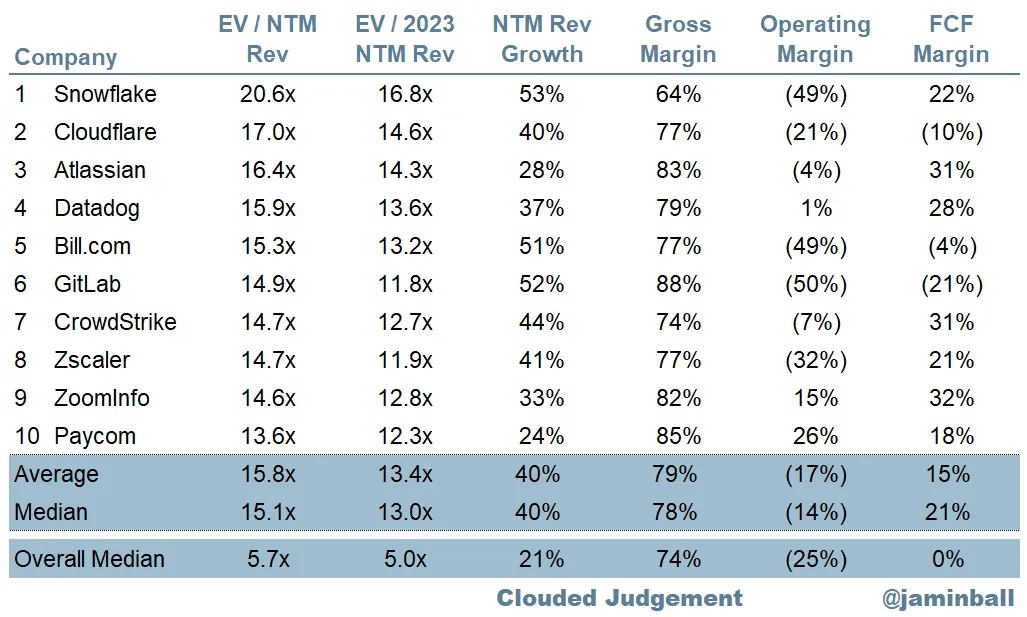
Its multiple, viewed in conjunction with the current environment we find ourselves in, requires the company to relentlessly execute in order to avoid a large rerating, a phenomenon that Cloudflare CEO Matthew Prince is quite excited about, as corroborated by the following from their most recent earnings call:
Matthew Prince Recession Comments (Author)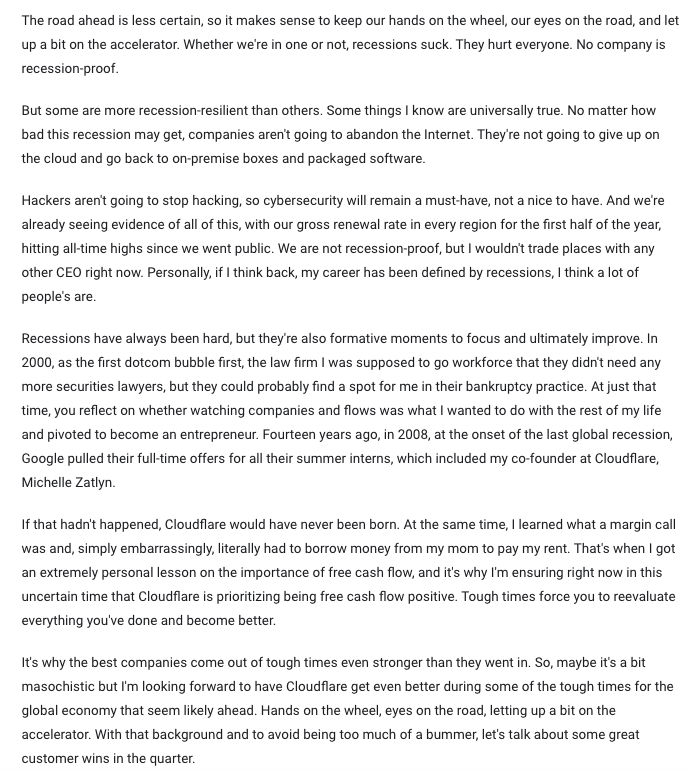
In order to gauge what exactly an idealistic scenario would result in share price-wise, I completed an extremely oversimplified DCF. With assumptions of a 20% Revenue Growth by 2030, 10% EBIT Margins, normalized tax, D&A, and CAPEX and NWC, an 8% WACC and 5% terminal growth rate, 2% reduction in SO per annum, and flat behavior in cash and debt (very idealistic), I arrived at an intrinsic share price of approximately $51.
Author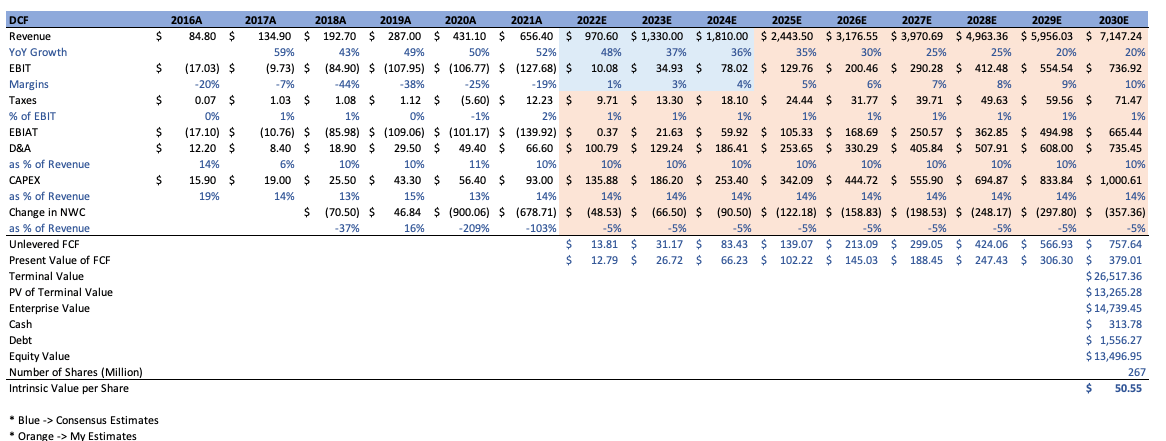
This exercise isn’t meant to convey forecasting accuracy, seeing as Cloudflare is a hypergrowth company that is inherently difficult to model. Rather, I am trying to illustrate that the company is expensive, even if a lot of things go right in an idealistic scenario over the course of the next few years.
Despite that fact, does that mean Cloudflare is untouchable as a company? In my opinion, no. Cloudflare has a series of competitive advantages that make them an undeniable powerhouse in each technical field they operate, as well as an engineering culture that has been fostered around expedient innovation, something that is hard to bet against. The company has forged relationships with network operators, and internet service providers and has undergone capex-intensive projects in order to build out network infrastructure that many will find hard-pressed to replicate, which is viewed in conjunction with the fact that every product can be run from every server across the company’s wide network, is a powerful proposition for clients. Their products are intertwined with mission-critical aspects of many customers’ operations. The company’s scale, combined with the fact that they have free product tiers, not only allows for them to cater to a wide audience, but also allows for widespread data collection that can be used for various improvement projects and optimization efforts. Cloudflare also has a vision for where technological trends are heading. Their R2 product is targeting a chink in the armour of how hyperscaler’s cloud offerings are set up and may very well takeoff. The company is evidently focused on pushing bundling on their customers, which should help them become indispensable as clients rely on Cloudflare for more and more functionality over the years. Cloudflare’s vision of Zero Trust is also shaping up. Not only are they leveraging different sales strategies to hit the ground running, but their acquisition playbook has already proven to have worked in this area. Area 51 offers Cloudflare the ability to bolster an email security product, something that is unique in this space and is not offered by a vast array of competitors. The bottom line? Cloudflare is one of the most exciting technology companies that exist today, even despite the lofty valuation.
Conclusion
Heading into a macroeconomic environment that continues to look bleak, we may start to see investment opportunities in tech companies that have extremely bright futures ahead. Cloudflare may very well be one of those instances, and I will be monitoring them for the foreseeable future as such.
Disclaimer: The information and research contained herein is all my own opinion and should not be used as a substitute for proper due diligence. Please consult your financial advisor and evaluate your financial circumstances before making any investment.
Disclosure (as of September 3, 2022): MT Capital Research holds no position in the securities discussed herein and does not anticipate to initiate a position in the forthcoming five days.
Editor’s Note: The summary bullets for this article were chosen by Seeking Alpha editors.


Be the first to comment